 |
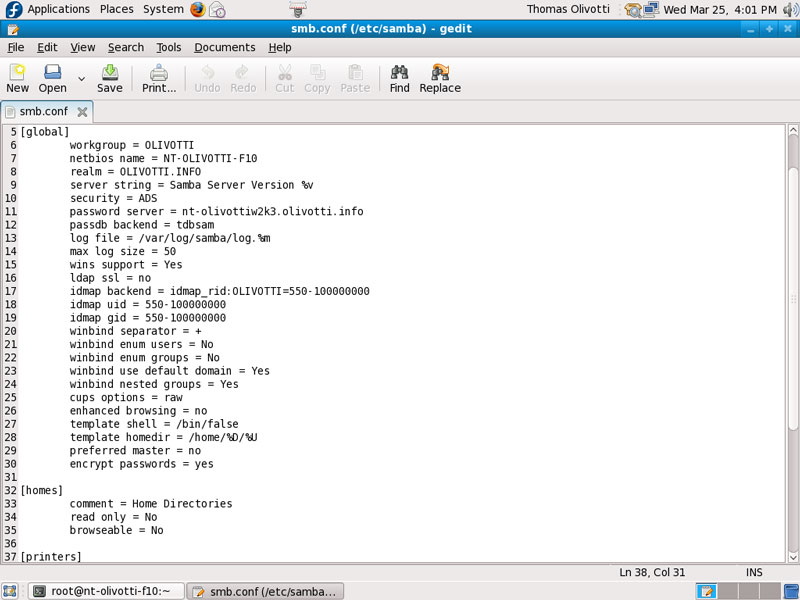
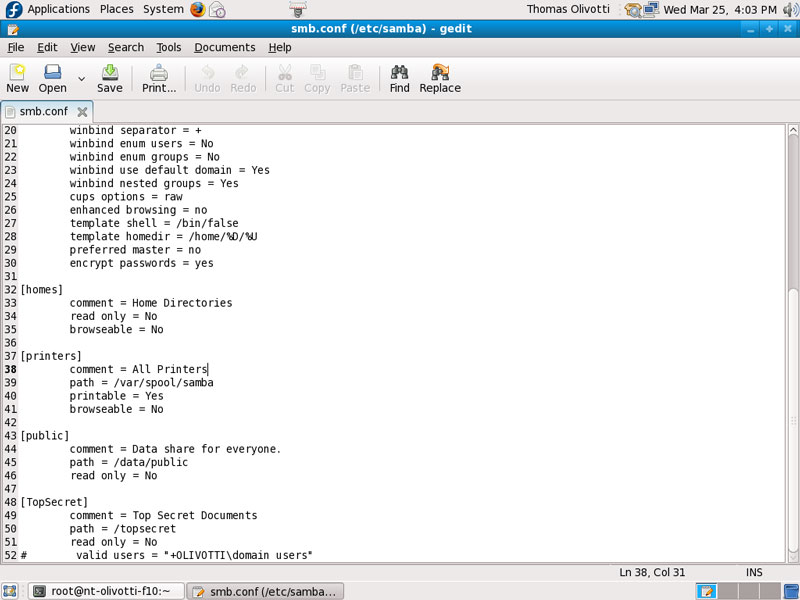
My Samba Configuration (smb.conf)
The first thing I did was set up a simple file share called public. Note my screen shots are after I integrated samba with kerboros
|
Click on Image
Click on Image
|
 |
Click on Image
|
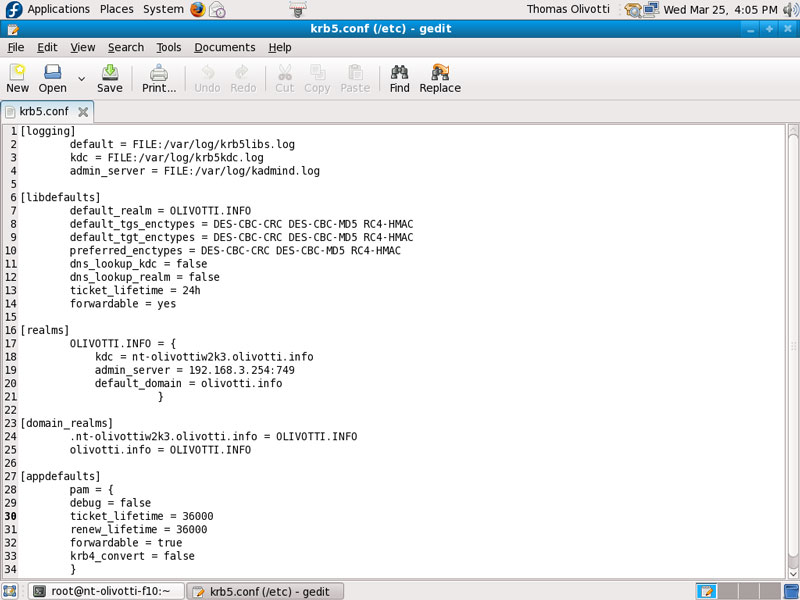
Integrating Kerboros
This was where I modified my krb5.conf file to integrate samba with kerboros.
|
 |
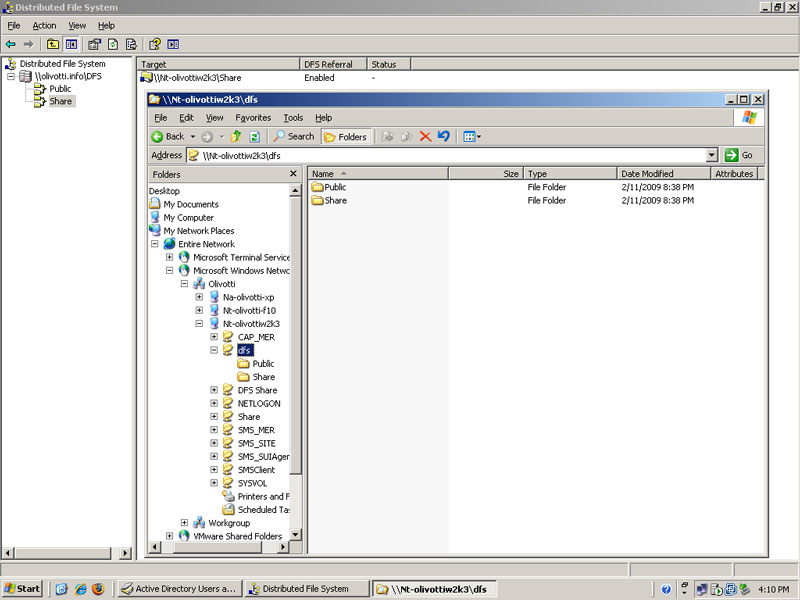
DFS (Distributed File System)
Now this is a really neat feature of Windows Server 2003. I created a file share on the windows server called share. I then combined the share on Linux with the share on Windows in a DFS.
|
Click on Image
|
 |
Click on Image
|
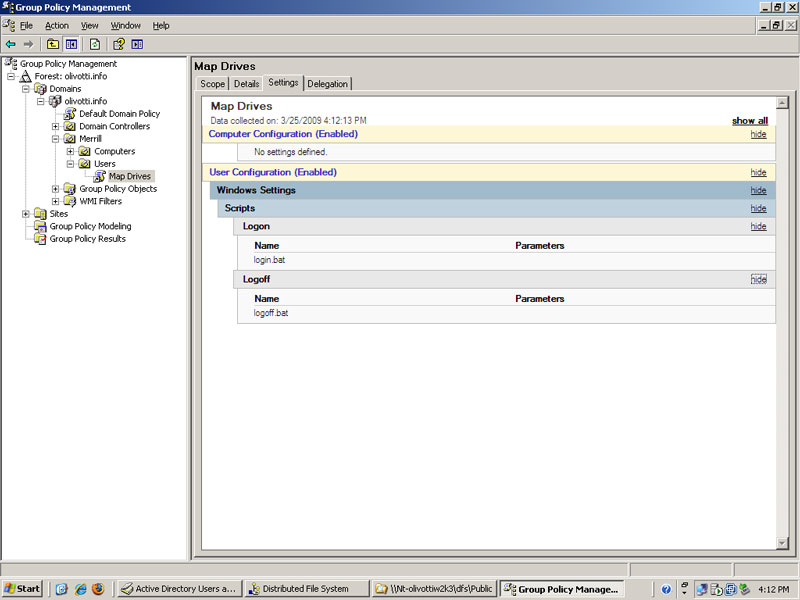
Group Policy Mapping
Now to give all my users access to the shares I used Group Policy in Active Directory. I created a login script to automaticaly map to the DFS Share on my Windows Server. The next thing I did was to create a log off script that would unmap the drive when users log off.
|
 |
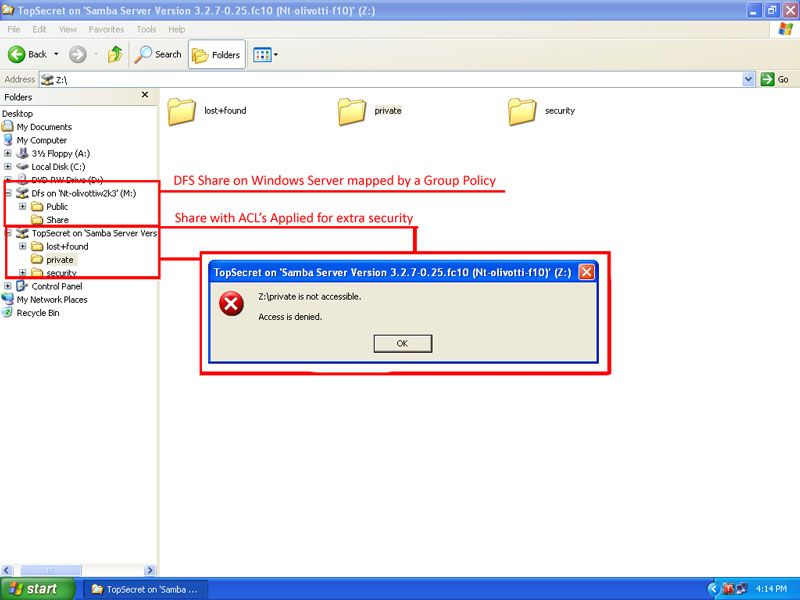
ACL's
In this part I added 3 hard drives and configured them in RAID 5. I then mounted the Raid Array with the ACL parameter. After setting permissions with the facl command and umask I made a private folder that normal users could not access. The private folder resides inside of a Topsecret share that users can access if they have proper permissions.
|
Click on Image
|
|