 |
TCPDump
In this exercise we checked to see that tcpdump was installed in Fedora. We then played around with some of the commands. Originally we were going to tie it into Nagios and automate capturing packets when a warning was set off. Due to time restraints we decided not to. This would have been a really fun exercise to complete though. Captureing packets during problem the time of the problem is ideal. Otherwise I would have to try and recreate the problem and begin capturing packets.
|
Click on Image
|
 |
Click on Image
Click on Image
Click on Image
Click on Image
|
Simulated Hacker Event
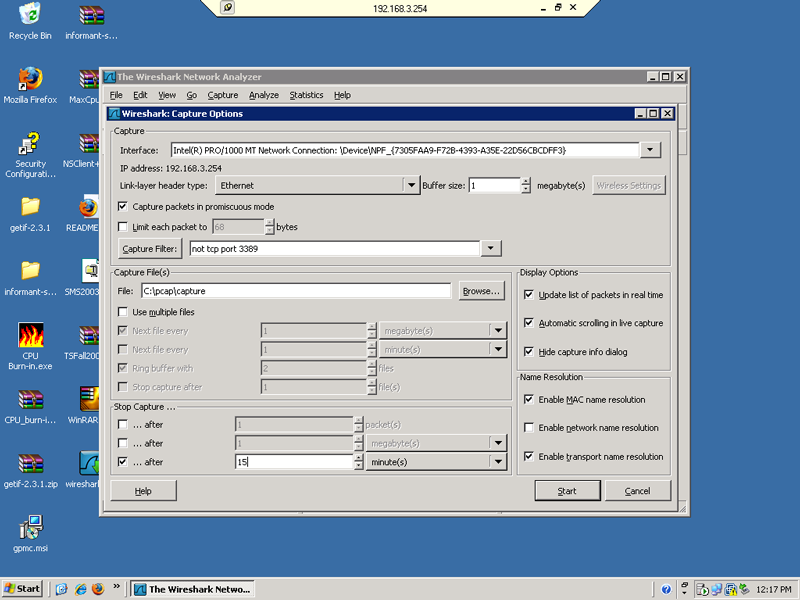
First I had to make sure that Wireshark was installed on my Windows Server. After that was done I remote desktoped in from Windows XP. I then started Wireshark and began capturing packets. I set the capture to last 15 minutes and then shut off. I also set it to save the capture file in C:/pcap/.
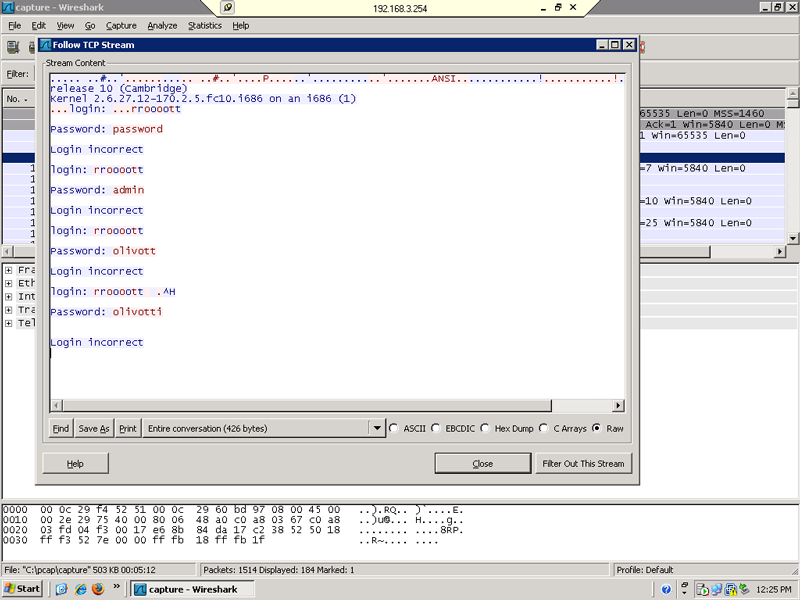
Next I got to play as a hacker. I switched to a Windows XP machine and started trying to access things on the network. First I accessed the intranet web page. From there I tried to access the Nagios GUI. I failed authentication a few times and gave up. So I tried to telnet to the Linux server and also failed authentication. Then I tried ftp with no luck. Next I accessed some network shares I was able to get to the shares but nothing of interest was there.
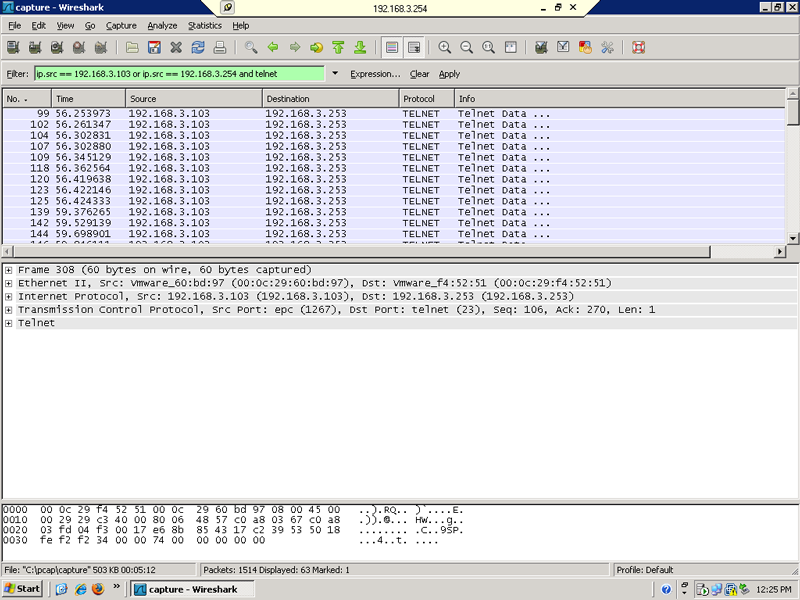
After all that fun stuff I went back to my normal IT role and waited for my Wireshark capture to stop. I then loaded my saved capture file into wireshark and began looking at the traffic. I used some filters and located some of the logon attempts and file share accesses.
|
|